Cyber Security At Honda Case Study Solution
First of all, to measure the current cyber-security position and strategy of Honda, the first component of the NIST framework i.e. Framework Core, has been analyzed. In this stage, the guidance information and the cyber-security activities, which are carried out by different industry players, are used in order to overcome the risks arisen by the cyber-security breach at Honda. The main essence of the framework core is that, it provides industry standards for dealing with risks associated with the cyber-security.
In addition, to evaluate the current cyber-security posture at Honda, the second component of the NIST framework i.e. Framework implementation Tier, has been followed in order to assess what cyber-security standards are best for catering the breach occurred at Honda. Finally, the last component of the NIST framework has been implemented, which enabled the security team to develop a blueprint, which has helped the team to minimize the cyber-security risks related to Honda’s organizational goals. It has helped the security team to detect the weak spots or the opportunities in order to improve the cyber-security system implemented at Honda.
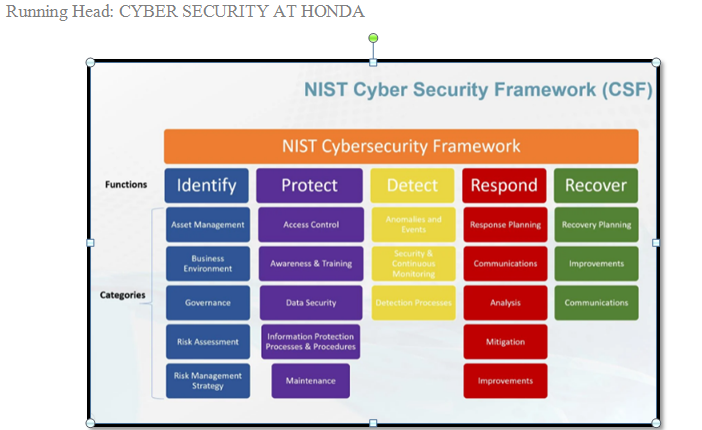
As the basis for US cyber-security standards and regulations that are beginning to emerge today, the NIST cyber-security structure is much important than before. The development of the National Cyber Security Framework is a public-private partnership led by NIST led by the President’s Executive Council to improve the security of critical infrastructure, and its core functions are rapidly expanding in scale and critical infrastructure-results-based The method enables it to operate on the scale of almost any industry. The NIST framework has three main poles: the core of the framework, the configuration file, and the implementation layer. Here, we will enter the core of the framework with five key functions: identification, protection, search, response, and search. NIST defines the core of the framework on its website as a set of network security functions, required results, and common operational references. All critical infrastructure areas. Core introduces departmental standards, guidelines, and practices to allow the integration of cyber-security pursuit and results across the entire organization, from management level to the highest performance level. The gap is classified according to capital expenditure and operating expenditure. Other relevant requirements are as follows:
NIST CSF: Identify:
NIST described Identify’s work in its first framework, which required “enhanced organization’s understanding of the management of cyber-security risks in systems, assets, data, and functions”. The focus is on the business and its relationship to network security risks, especially considering the resources used. The work of NIST Identify lays the foundation for actions your organization takes to advance cyber-security(Hall, 2020). Determining the resources available, the risks associated with these areas, and how they relate to your business background and goals are critical to the success of the framework. The successful implementation of the identification function leads the organization to strictly abide by all assets and facilities outside the enterprise, defines the current and required control measures to protect these funds, and protect the system from current to required security conditions. The result is that stakeholders in both technology and business processes have defined a well-defined organizational security posture.
NIST Protect:
NIST stated that in general, the framework is committed to clarifying the organization's security risk management through data planning, data sharing, supporting cyber-security risk management decisions, improving learning, and responding to threats through past activities. Protect’s work is important asit’sgoal is to develop and apply appropriate protective measures to ensure the provision of reliable basic services. The defense function protects the aptitude to limit or control the impact of potential network security incidents. The more the identification is concerned with infrastructure and monitoring, the more secure the framework. Protect's work cover category such as approach control, awareness and training. Display of these areas and function of overall protection are embodied in two or more verification procedures to control access to property and facilities and employee training to lessen risk of accidents and community violations that occur in the community.
As violations become more common, it is important to apply appropriate policies to reduce the risk of violations. The function of the protection framework can serve as a guide and guide the results required to achieve this goal.
Detect:
Detection needs to perform appropriate actions to detect the event of a network security incident. "The detection function can detect network security events in time. Examples of the results of this operation include anomalies and events; continuous security monitoring; and acquisition procedures."
- Confusion and Events:
The program will quickly detect abnormal activity, and the impact of the incident will be understood by everyone on the team and others who may be involved.
- Continuous Security and Monitoring:
Monitoring information systems and locations from time to time to identify cyber events.
- Discovery Procedures:
Develop and evaluate discovery procedures and procedures to ensure that detailed information about cyber incidents is provided in a timely manner. Detection is a key step in a powerful network system-if a network event is detected quickly, the results can be reduced immediately.
- UniqueEvents:
Give your team the experience to collect and inspect data from various locations to find incidents.
- Continuous Security and Monitoring: Enable your team to monitor your assets.
- Detection Procedures
Try to understand the violations as soon as possible and follow the relevant requirements. Your system should be able to quickly detect improper access to data.
The discovery of violations or incidents may be a matter of life and death for your business, which makes the work of "detecting cyber-security frameworks" very important to the success and success of your business.
Respond:
NIST describes the task of responding as "Develop and implement appropriate actions to take action in relation to a cyber-security incident detected."
"Response work supports the ability to control the impact of potential cyber-security incidents. Examples of this work product area include response planning, communication, analysis, mitigation, and development." Response work uses response plans, analysis, and easing measures to ensure that the cyber-security system is in state of uninterrupted improvement. The beginning of the accountability program is an important first step in accepting accountability-verifying the agreement with the required reporting requirements that are encrypted and securely delivered to a given industry. The best next step is to reduce the plan-what steps will your team take to deal with the risks identified in the plan and organization?
Recover:
Then, the core of the framework determines the key and category of each activity, and is consistent with exemplary guiding guidelines (such as living standards, guidelines and practices (NIST) at each stage). According to NIST, recovery is defined as "the need to create and perform appropriate activities to maintain a robust system and restore any skills or services that will not be compromised by a cyber-security incident. The recovery function supports timely recovery from daily tasks to maximize Minimize the impact of cyber-security incidents. Examples of the results of this work include reorganization, development, and communication.
Refunds include the following locations:
- Recovery Plan
Recovery processes are tested, performed, and then it stored so that your system can alleviate event results sooner
- Improvements
Redesign and processes are made better when events take place, and areas for improvement are specified and their relevant solutions are integrated...............
Cyber Security At Honda Case Study Solution
This is just a sample partial case solution. Please place the order on the website to order your own originally done case solution.